LSE Summer Week - July 16 - July 18 2013
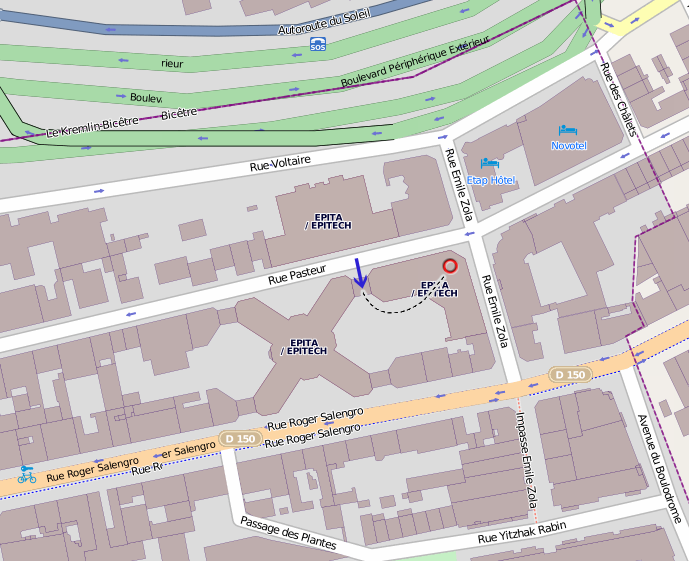
Lieu et plan d'accès
Amphithéâtre 4, EPITA, 24 rue Pasteur, 94276 Le Kremlin-Bicêtre.
Transports en commun : métro 7 (station Porte d'Italie), bus 47/125/131/185/186 (station Roger Salengro-Fontainebleau).
Planning Complet
Tuesday 16
Introducing the LSE Week
19h30 19h35Non Interference Property - Marwan Burelle
19h35 20h05Based on trace-theory approach, the non-interference property is a fundamental property used in field like parallelism or language level security. This talk will be a walk through techniques used in theoretical information flow security and a little introduction to a use in parallel programming Slides Video Youtube
Building Reliable Services on top of Untrustworthy Large Scale Decentralized Networks - Julien Quintard (Guest)
20h10 20h55This talk addresses the problems inherent to open large scale decentralized i.e peer-to-peer networks and how to create reliable services though based on a set of untrustworthy machines via Byzantine fault tolerant algorithms and protocols. Slides Video Youtube
mikro - Introducing a C++ Mikro Kernel - Victor Apercé & Julien Freche
21h00 21h30Overview of the mikro kernel. We will introduce the notion of microkernel and some major singularities of this design. We will talk about the benefits and drawbacks of writing a kernel in C++ and some design considerations when using objects in kernel. We will explain some of the solutions that we are using in the mikro kernel. Slides Video Youtube
mikro - About Paging - Victor Apercé
21h35 22h05About everything you should know to deal with paging on x86: from hardware management to algorithms. Linux and mikro choices will be explained. Slides
mikro - Efficient Inter Process Communication - Victor Apercé & Julien Freche
22h10 22h30Overview of inter process commnunications in different kernels and what this implies in terms of performance. We will then introduce the specific design chosen for the mikro kernel. Slides
mikro - Multiprocessor Init in Kernel - Julien Freche
22h35 22h55This talk will deal with multiprocessor initialization on x86. I will introduce the notion of Bootstrap processor and application processor and explain how to detect the cpu topology (number of threads, cores and cpus). We will also see how to boot an application processor and set up a per-cpu storage in kernel. Slides Video Youtube
Wednesday 17
HOWTO: Boot an OS - Camille Lecuyer (Guest)
19h30 20h00We will see what happen when we boot a computer, existing methods and protocols. Today, the main methods to boot an OS are via the BIOS (with MBR) and via the new way, UEFI. The goal of this talk is to understand what bios and UEFI provide, why today we can use UEFI and how to use both of them. We will explain also how to boot a Linux kernel and a Multiboot kernel. Slides Video Youtube
Machine Learning Applied to Process Scheduling - Benoît Zanotti
20h05 20h25Process scheduling is a complex process: whereas algorithms try to be as efficient as possible in the general case, there is always room to improve on specific applications. We will see how we can use machine learning to exploit datas from past executions to improve general case scheduler on specific applications. Slides Video Youtube
Networking in STOS - Ivan Delalande
20h30 21h00Presentation of the development of a networking IP stack from the lower layers: summary on e1000 device driver, ethernet and IP layers. Description of the problems encountered during this develpment (APIC…). Slides Video Youtube
v8086, Execute 16bit Code in Protected Mode - Corentin Derbois
21h05 21h25We will see in this talk how to execute 16bit code when the protected mode and pagination are on. Mainly, we will talk about the virtual mode 8086 provided by Intel, how it works exactly, and finally its advantages and disadvantages. Slides Video Youtube
Hardware/Software Solutions to x86 Virtualization - Marc Angel & Corentin Derbois
21h30 22h15We will see hardware solutions provided by Intel and AMD to manage multiple virtual machines, from the instruction set, to the hardware resource management. In a second part, we will introduce some exemple of guest/host communication systems and virtualized devices. Slides Video Youtube
KVM without Qemu - Gabriel Laskar
22h20 22h50How can we create a virtual machine without any emulated hardware? This talk will expose the kvm api and how we can interact between a virtual machine and kvm. Slides Video Youtube
Thursday 18
HOWTO: Basic Vulnerabilities and their Exploitation - Samuel Angebault
13h30 14h15Bugs like buffer overflow, format string and use after free are often introduced by a wrong usage or bad coding practices. This talk will explain how to recognize and exploit them. It will also explain the security mechanisms developed and how to bypass them. Slides Video Youtube
Order Is a Lie - Marwan Burelle
14h25 15h10How can we understand and correctly use the complexity of memory accesses in modern super-scalar mutlicore processor? From memory barrier to non-blocking algorithm (lock-free/wait-free) and maybe more … Slides Video Youtube
Helping Reverse Engineering with LLVM - Lionel Auroux
15h20 16h05Reversing assembly code is a tricky task and could be slowed by assembly code obfuscations. To help this task, we propose to use the LLVM intermediate language as target of a decompilation tool. We will analyse benefits and defects of this technique with some practical examples. Slides Video Youtube
The Hell of x86 Kernel Debugging - Clément Rouault
16h15 16h45This talk aims to explain some peculiarities of the X86 architecture and the RING0 and how to use them as anti-debug techniques. The Goal is also to exhibit some limitations of GDB or emulators like QEMU. Some scripts to ease the debug on x86 using GDB Python will be introduced. Slides Video Youtube
Advanced Python Features Gone Bad - Franck Michea & Clément Rouault
16h55 17h25Dive with us into the complexity of dynamic languages, with the example of Python. We will introduce techniques that could be used to obfuscate the control flow of a program using some of the advanced features provided by Python. This talk will also speak about internal structures and implementations of the main interpreter, and how to play with them. Slides Video Youtube
A Look into the Windows Kernel - Bruno Pujos
17h35 18h20Presentation of the evolution of the security inside the Windows kernel, between Windows XP and Windows 8. The talk will be illustrated with the demonstration of two exploits, one on Windows XP and one on Windows 8. Slides Video Youtube
Concolic Execution - Jonathan Salwan (Guest)
18h30 19h15We will talk about concolic execution using Valgrind and Z3. Concolic execution is a technique that uses both symbolic and concrete execution to solve a constraint path. Valgrind is a Dynamic Binary Instrumentation framework, you can easily build dynamic analysis tools. It also uses a RISC-like intermediate language called VEX. Z3 is a high-performance theorem prover developed at Microsoft Research. Slides Video Youtube