LSE Summer Week - July 7 + July 9 2022
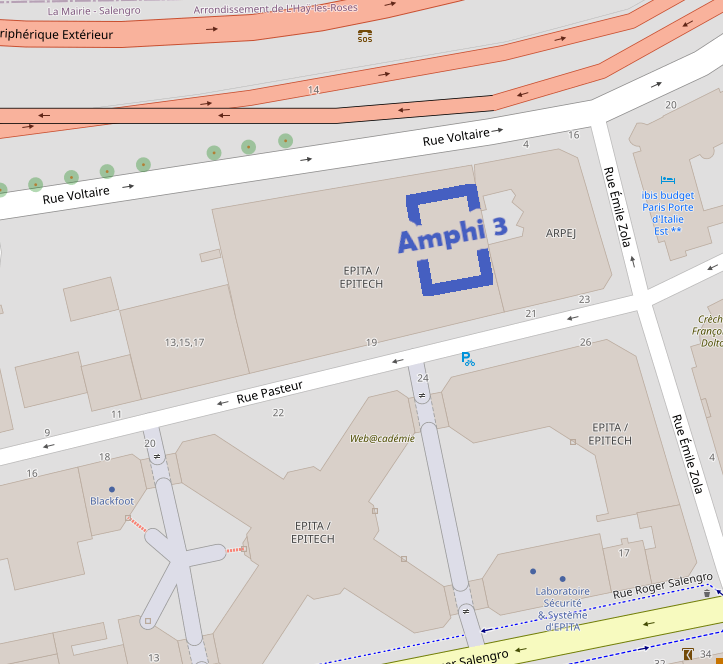
Lieu et plan d'accès
Amphithéatre 3, EPITA, 24 rue Pasteur, 94276 Le Kremlin-Bicêtre.
Transports en commun : métro 7 (station Porte d'Italie), bus 47/125/131/185/186 (station Roger Salengro-Fontainebleau).
Thursday 7
Trusted AI for secure critical systems - Pierre Parrend
10h00 10h45Presentation of the LSE teams and the current work Pierre is involved in Slides
Generating synthetic traffic to improve the robustness of network intrusion detection - Grégory Blanc
10h45At the first level, Security Operations Center focus on triaging alerts raised by intrusion detection probes. With the emergence of new and evasive attacks, there is a need to develop anomaly-based detectors able to capture deviations from a known, nominal behaviour. Lately, machine learning, and then, deep learning have been largely exploited to produce models of traffic able to capture these legitimate traffic patterns. In operations, training these models require a source of legitimate traffic that is often hard to come by. And the absence of legitimate traffic is also detrimental to their evaluation. This is why a recent research trend has emerged proposing to generate synthetic traffic for augmenting training and testing datasets with legitimate samples that are important to prevent overfitting. Indeed, false positives that arise from previously unseen legitimate behaviour may result in additional noise for security operators. Conversely, a similar yet very different approach has led researchers to question the robustness of such detectors by generating evasive samples, known as adversarial examples. In this presentation, we will be presenting our first attempts at generating traffic data to tackle both problems. Slides
Industrial communication with 0PC UA - Secure by design? - Julius Pfrommer
11h15Industrial Communication with OPC UA - Secure by Design? OPC UA is the leading protocol for industrial communication in factory automation. As industrial networks become larger and connected to the internet, OPC UA comes equipped with a range of security measures to protect data and the continuous operation. This talk introduces OPC UA and the security measures defined in the standard. This is contrasted with insights from the open62541 implementation by the author (and team) and the experience of practical deployments with industrial partners. Slides
Port scans and DDos detection by time series filtering - Mark Angustures
11h45Most network intrusion detection systems rely on signature-based methods and labeled data, but systems based on anomaly detection algorithms promise to detect unseen attacks without labeled data. However, anomaly detection on streaming data is a challenging task because real networks generate an endless stream of fast and high volume data. In this talk we propose an anomaly detection system for detecting port scan and DDoS anomalies in streaming NetFlow data. We extract features through different key combination of NetFlow aggregations. Within these aggregations we tried multiple sets of features to find the optimal ones for detection. We computed Kalman filter and prediction interval on time serie of each feature, detecting attacks as outliers. We set up a MapReduce architecture using spark and Kafka to handle high-speed and high-volume data. Our experimental results show our anomaly detection algorithms as very promising for rapidly detecting port scans and DDoS.
Vulnerabilities, risks, and countermeasures in IoT environments - Badis Hammi
14h00In the context of current smart cities, Cooperative Intelligent Transportation Systems (C-ITS) represent one of the main use case scenarios that aim to improve peoples' daily lives. Thus, during the last few years, numerous standards have been adopted to regulate such networks. Within a C-ITS, a large number of messages are exchanged continuously in order to ensure that the different applications operate efficiently. However, these networks can be the target of numerous attacks. The sybil attack is among the most dangerous ones. In a sybil attack, an attacker creates multiple identities and then disguises as several fake stations in order to interfere with the normal operations of the system or profit from provided services. We analyze recently proposed sybil detection approaches regarding their compliance with the current C-ITS standards as well as their evaluation methods. We provide several recommendations such as network and attack models as well as an urban and highway datasets that can be considered in future research in sybil attack detection. Slides
Anonymisation of DNS requests through blockchain - Yves Elloh
14h45Le système de noms de domaine ou DNS est un service informatique distribué utilisé pour traduire les noms de domaine Internet en adresses IP ou autres enregistrements. C'est l'un des protocoles critiques pour le bon fonctionnement de l'Internet actuel. Le DNS a été pendant longtemps ciblé par plusieurs attaques comme: les attaques d'empoisonnement du DNS, l'attaque d'amplification DNS etc. Un utilisateur malveillant ayant accès aux requêtes/réponses DNS d'un client pourra profiler ce dernier, Notamment ses habitudes, ses intérêts, etc. Ce serait une grave atteinte à sa vie privée. L'attaquant pourrait autant être une entité externe à la communication qu'un intermédiaire tel qu'un FAI ou un fournisseur de services DNS. Il existe différentes solutions pour authentifier, protéger l'intégrité et la confidentialité des requêtes DNS comme: le DNSSEC, DNSCRYPT, DNS-over-HTTPS (DoH) etc. Malheureusement, toutes ces solutions ne protège pas contre un intermédiaire malveillant, notamment un FAI agissant à des fins commerciales. Nos travaux visent à concevoir un protocole de sécurité basé sur la blockchain. Slides
Malware - Mohammed Badreddine Zouhair
15h30
Cartography of submarine zones with lightweight means - Loïca Avanthey and Laurent Beaudoin
16h45
Saturday 9
Discovering new ways of attacking AES when trying to do something else - Martin Grenouilloux
14h00A promising attack on AES on an algebraic level can be done by computing the corresponding Gröbner basis. However, this method is slow and inneficient but it can certainely be improved upon. This talk is about algebraic cryptanalysis and my work on the subject, and how, when searching to improve this algorithm, we found another angle of attack on AES using graphs. Slides
Work on an UEFI driver rootkit with a bare metal hypervisor - Alex Levigoureux and Antoine Jouan
14h45UEFI aims to replace BIOS. It has a feature called UEFI drivers, which can be a good place to install rootkit. UEFI drivers are executed before the operating system and has full privilege over the system. Virtualizing an operating system makes the rootkit hard to detect... Slides
Writing a bare metal GPU driver for the Raspberry PI 4 - Darius Engler
15h45The Raspberry PI 4 is a great board for experimenting with OS development. However, one thing that appears to be lacking is good documentation about some specific parts of the board. The GPU is one of these parts, and in this talk, I will discuss how I managed to write a bare-metal driver capable of rendering graphics by digging in Linux and Mesa and what problems I encountered along my path. Slides
Secure user-defined abstractions using exokernels - Daniel Frederic
16h30Rump session
17h30