LSE Summer Week - July 14 - July 16 2016
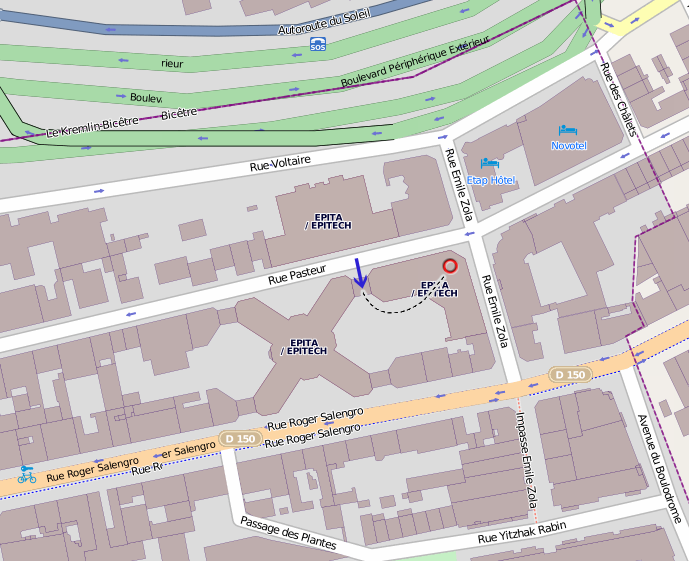
Lieu et plan d'accès
Amphithéâtre 4, EPITA, 24 rue Pasteur, 94276 Le Kremlin-Bicêtre.
Transports en commun : métro 7 (station Porte d'Italie), bus 47/125/131/185/186 (station Roger Salengro-Fontainebleau).
Thursday 14
Introducing the LSE Week
13h55
Do Machines Dream of Binary Files - Marwan Burelle
14h00 14h45Deep learning techniques offer a lot of appealing results on a wide variety of data, my goal is to apply these techniques to binary executables. I'll explore auto-encoders and deep-networks in order to encode machine code extracted from binary files and construct learnt graphs for clustering and classification. To illustrate my experiments, I'll show you some results with source files' remapping, program classification and malware classification. Slides Youtube
Angry Module Excavation - Stanislas Lejay
14h45 15h30angr and I will join forces in a quest through anarchy, reversing compiled kernel modules to tear their beloved ioctls down… Slides Youtube
Medusa a disassembler and something more… - Angelin Booz (guest)
15h45 16h15Medusa was designed to be a modular and interactive disassembler. Actually, It's a little bit more, It's a tool for pragmatic binary analysis. We'll see why some reverse engineers turned coffee into Emulation and Symbolic Execution engine for fun and profits. Slides Youtube
Automated generation of volatility Linux profile - Alpha Abdoulaye
16h15 16h45Unlike on Windows where we have a reasonable number of variations, memory analysis on Linux can prove to be difficult. In fact, there is a significant amount of different distibutions and versions of Linux, which makes them quite difficult to be analysed in a unified way. Using Volatility, one should provide profiles corresponding to the dumps' kernel versions and distributions. We'll see how to try to simplify the analysis by automating the profile generation. Slides
Heapster Eggs - Matthieu Tardy
17h00 17h45After an overview of malloc internals, we will discover some of the hidden memory corruption features provided by malloc. Slides Youtube
Windows kernel exploitation techniques - Adrien Garin
17h45 18h30Presentation of some exploitation techniques used for privilege escalation and code execution on the Windows kernel through vulnerable drivers. We will see several mitigations implemented by Microsoft. Slides Youtube
Reverse-engineering the bitstream of Altera's MAX-V CPLDs - Jean-François Nguyen Thanh Nhan
18h45 19h30
After an overview of the design flow for CPLDs and the internals of the MAX-V, we will see how one can profit from the non-determinism of the place-and-route algorithm in order to isolate the bits relevant to each logic cell of the CPLD.
The goal of this process is to be able to retrieve the underlying RTL netlist of a bitstream by analyzing it.
Slides
Youtube
Friday 15
Can Strace make you fail? (talk in english) - Nahim El Atmani
19h30 19h50While you sleep, strace is getting a brand new feature thanks to the GSoC. Strace fault injection will soon let you discard its target's syscalls based on your craziest desires. After a quick implementation review, you will meet your new best companion through this fuzzy quest. Slides Youtube
How applications can communicate on Android? - Antoine Damhet
19h50 20h10A look into the binder kernel driver, how to trace these communications and how to catch them for further fun stuff. Slides Youtube
Intel Open Network Platform - Lionel Auroux
20h15 21h00An overview of Intel ONP thru some Software-defined networking examples: DPDK, DPI, IPS... Slides Youtube
Virtual memory in STOS - Pierre Marsais
21h15 21h35In most operating systems, memory management have features such as file mapping, memory protection and copy on write. Here's a way to implement those features for STOS. Slides Youtube
Build a USB 2.0 device from scratch - Philémon Gardet
21h35 21h55Presentation of a USB serial device implementation on an FPGA board. In this regard, the different layers of protocols from electronic to software levels used will be explained. Slides Youtube
Saturday 16
Be paranoid or not to be ? - Alizée Penel (guest, talk in english)
14h00 14h45Since last Android release, Internet permission level changed from “dangerous” to “normal” level, letting most of users and developers anxious about the security of their devices. What is really happening inside Android OS when an Internet connection is made ? What does that implies in term of security ? Do we have to be paranoid regarding this matter ? Through this talk, we are going to reveal the truth about Android sockets and their consequences. Slides Youtube
About unchecked management - Bruno Pujos (guest)
14h45 15h30The System Management Mode (SMM) is still an obscure and amazingly powerful mode today. Its features made it really interesting for an attacker: more privileges than the system and invisible from it. This presentation will explain the basics of this mode and go into details about the exploitation of a unchecked pointer vulnerability present in several OEMs. It will also describe the patch and discuss how it should have been done. Slides Youtube
One Device to drive them all - Pierre Surply
15h45 16h30
Three Devices for logic analysis of passively captured traces,
Seven for inter-chip communication driven by hardwired interfaces,
Nine for in-circuit debugging limited to specific purpose,
One for complex hardware reverse engineering scenarios
Une analyse pour détecter les violations de strict aliasing - Pascal Cuoq (guest)
16h30 17h15
La règle du strict aliasing, présente dans le standard C depuis C89, n'est pas très connue dans le monde des développeurs C. Or, les principaux compilateurs (GCC et Clang) mettent cette règle à profit pour effectuer des optimisations agressives, quite à ce que le code optimisé ne corresponde pas à l'intention du développeur ignorant ces subtilités.
La méconnaissance de la règle et la recherche de performance des compilateurs peut donc causer des problèmes difficile à localiser (cf. le noyau Linux), éventuellement ayant des conséquences sur la sécurité.
Pour détecter les violations de la règle du strict aliasing, une analyse est en cours de mise au point au sein de l'analyseur statique TIS Analyzer, qui formalise la règle de strict aliasing, et vérifie que le programme analysé la respecte.
Slides
Youtube
OpenBSD rc.d(8) - Antoine Jacoutot (guest)
17h30 18h15
OpenBSD has always used the traditional static BSD initialization script: /etc/rc. While dependable, it did not allow for easy integration with monitoring, configuration management software and/or any kind of tools requiring automated service handling. rc.d(8) was developed to abstract service management while pertaining the existing behavior like predictive and sequential start-up ordering (dependency-less).
The way OpenBSD boots hasn't changed much since its inception. This presentation will describe the OpenBSD rc.d(8) framework and rc.subr(8) daemon control routines. While it resembles other implementations, it was written from scratch to match the project objectives (simple, ordered, non-intrusive). I will describe the internals of rc.subr and talk about the implications that it had on the traditional BSD start-up sequence.
I will then introduce rcctl(8): an all-in-one utility for managing rc(8) daemons and services.
Slides
Youtube
proot, simplifying ports builds on OpenBSD - Marc Espie
18h15 18h45
doing manual chroot builds of packages is a nice joke. It requires a lot of skills, and is error-prone.
proot was designed to help simplify that process. As usual, going from a personal idiosyncratic framework to a production ready tool was an interesting experience. It is a balancing act between being as simple as possible (and damn-fool proof) and still rich enough to cater for most situations.
Slides
Youtube
Rump Session
19h00 20h00
Slides for some of the rumps:
Life of an instruction in clang/llvm (Francis Visoiu Mistrih)
Let's play with signals (Gabriel Laskar)
Barbecue
20h00